State Of Nature Node Shape
Abstract
Time to come quantum internet applications will derive their power from the ability to share breakthrough data across the network1,2. Quantum teleportation allows for the reliable transfer of quantum information between distant nodes, even in the presence of highly lossy network connections3. Although many experimental demonstrations have been performed on different quantum network platforms4,5,six,7,eight,ix,10, moving across direct connected nodes has, and so far, been hindered past the demanding requirements on the pre-shared remote entanglement, joint qubit readout and coherence times. Hither we realize quantum teleportation between remote, non-neighbouring nodes in a breakthrough network. The network uses three optically continued nodes based on solid-land spin qubits. The teleporter is prepared by establishing remote entanglement on the ii links, followed past entanglement swapping on the middle node and storage in a retention qubit. Nosotros demonstrate that, one time successful preparation of the teleporter is heralded, arbitrary qubit states tin can be teleported with allegiance above the classical jump, even with unit of measurement efficiency. These results are enabled by cardinal innovations in the qubit readout procedure, active memory qubit protection during entanglement generation and tailored heralding that reduces remote entanglement infidelities. Our piece of work demonstrates a prime building block for future quantum networks and opens the door to exploring teleportation-based multi-node protocols and applications2,xi,12,13.
Master
Quantum teleportation is the central routine for reliably sending qubits beyond lossy network links3, as well as a key primitive of quantum network protocols and applicationsii,11,12. Using a teleporter in the class of a pre-shared entangled country, the quantum data is transferred past performing a joint Bell-state measurement (BSM) on the sender's part of the entangled state and the qubit state to be teleported. The land is recovered on the receiving node past a gate operation conditioned on the BSM outcomethree. Considering the quantum information is non transmitted past a concrete carrier, the protocol is insensitive to loss in the connecting photonic channels and on intermediate nodes. A deterministic BSM combined with existent-fourth dimension feed-forward enables unconditional teleportation, in which state transfer is accomplished each time a qubit country is inserted into the teleporter.
Pioneering explorations of breakthrough teleportation protocols were performed using photonic states4,five,six. Following the development of quantum network nodes with stationary qubits, remote qubit teleportation was realized between trapped ions7, trapped atoms8,x, diamond nitrogen-vacancy (NV) centres9 and memory nodes based on diminutive ensembles14.
Although future quantum network applications will widely use teleportation between non-connected nodes in the network, the demanding set of requirements on the pre-shared entanglement, the BSM and the coherence times for enabling real-time feed-forward has, so far, prevented the realization of teleportation beyond directly connected stationary network nodes.
Here we overcome these challenges past a set of key innovations and achieve qubit teleportation betwixt non-neighbouring network nodes (come across Fig. 1a). Our quantum network consists of iii nodes in a line configuration, Alice, Bob and Charlie. Each node contains a NV center in diamond. Using the NV electronic spin as the communication qubit, we are able to generate remote entanglement between each pair of neighbouring nodes. In addition, Bob and Charlie each use a nearby 13C nuclear spin as a memory qubit. The steps of the teleportation protocol are shown in Fig. 1b. To prepare the teleporter, we utilize an entanglement swapping protocol mediated by Bob, like to a breakthrough repeater protocolxv, to institute entanglement between Alice and Charlie. Once successful training of the teleporter is heralded, the input qubit country is prepared on Charlie and finally teleported to Alice.
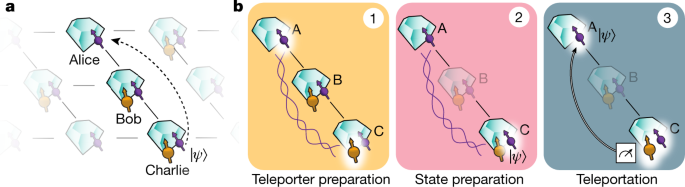
a, Three network nodes, Alice (A), Bob (B) and Charlie (C), are connected by means of optical fibre links (lines) in a line configuration. Each setup has a communication qubit (purple) that enables entanglement generation with its neighbouring node. Furthermore, Bob and Charlie incorporate a retentiveness qubit (yellow). b, The steps of the teleportation protocol. (1) We prepare the teleporter past establishing entanglement between Alice and Charlie using an entanglement swapping protocol on Bob, followed past swapping the country at Charlie to the retentivity qubit. (2) The qubit country to be teleported is prepared on the advice qubit on Charlie. (three) A BSM is performed on Charlie's qubits and the outcome is communicated to Alice over a classical channel. Dependent on this outcome, Alice applies a quantum gate to obtain the teleported qubit state.
Entanglement fidelity of the network links
A key parameter for quantum teleportation is the allegiance of the pre-shared entangled state between Alice and Charlie. As nosotros generate this land by entanglement swapping, its allegiance can exist increased by mitigating errors on the individual links. Our network generates entanglement between neighbouring nodes using a single-photon protocolsixteen,17 in an optical-phase-stabilized architecture18. The building cake of this protocol is a qubit–photon entangled state created at each node. To generate this entangled country, we initialize the advice qubit in a superposition state \(|\psi \rangle =\sqrt{\alpha }|0\rangle +\sqrt{1-\blastoff }|i\rangle \) and apply a country-selective optical pulse that transfers the population from \(|0\rangle \) to an optically excited state. Following spontaneous emission, the qubit state is entangled with the photon number (0 or i photon). Nosotros perform this protocol on both nodes and interfere the resonant photonic states on a beam splitter (Fig. 2a). Detection of a single photon in ane of the output ports ideally heralds the generation of an entangled country \(|\psi \rangle =(|01\rangle \pm |10\rangle )/\sqrt{2},\) in which the ± phase is gear up past the detector that clicked. Figure 2b shows the joint outcomes of qubit measurements in the computational ground later entanglement is heralded, showing the expected correlations.
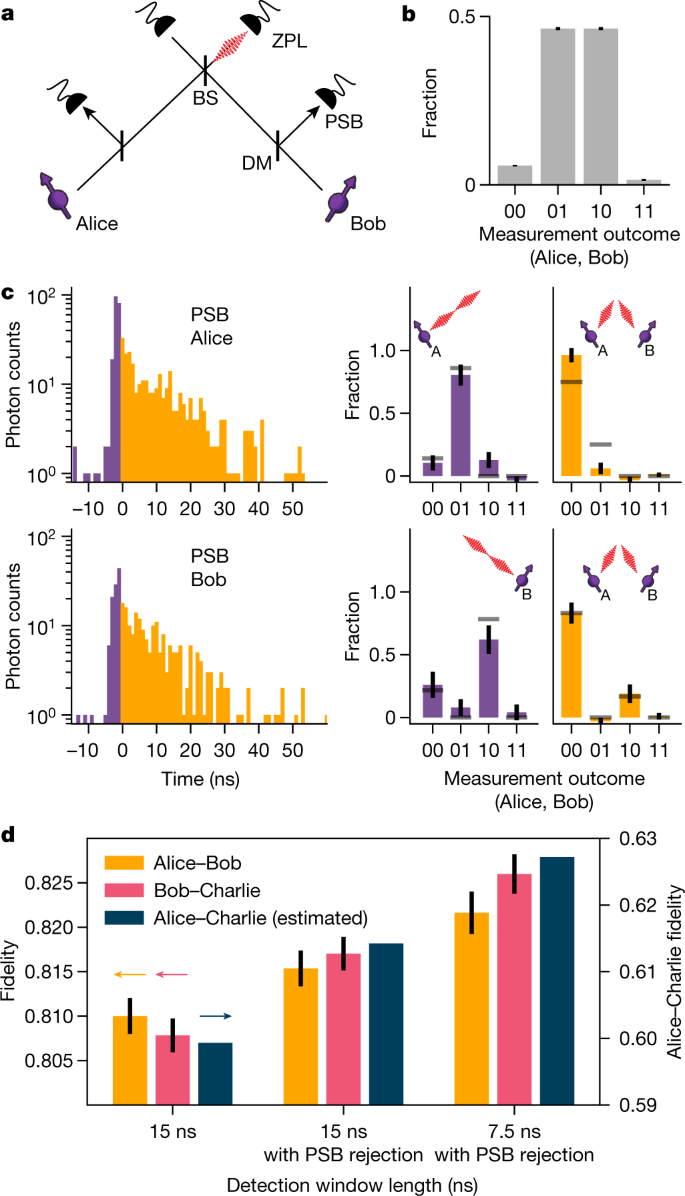
a, Simplified schematic of the optical link used for generating entanglement betwixt neighbouring nodes. Photons emitted by the communication qubits are filtered past a dichroic mirror (DM) to carve up the resonant (null-phonon line, ZPL) photons (three% of emission) from the off-resonant (phonon-side ring, PSB) photons (97% of emission). The resonant photons are sent to the beam splitter (BS); detection of a unmarried photon at 1 of the ZPL detectors heralds successful generation of an entangled state between the two nodes. b, Measured correlations of the advice qubits in the computational basis, conditioned on a heralding issue on the ZPL detectors. c, Left, histograms of the PSB photon detection times on Alice (top) or Bob (bottom), conditioned on a simultaneous ZPL detection in the same entanglement generation endeavour. Grey lines prove expected correlations on the ground of a breakthrough-optical model (run across Supplementary Information). The correlations measured in the other measurement bases tin can be found in Extended Data Fig. 1. d, Measured fidelity of the network links, without PSB rejection (left), with PSB rejection (center) and with PSB rejection plus shortened detection window (right). The dark blue bars bespeak the respective expected allegiance on Alice–Charlie after entanglement swapping for each case (run across Methods). All fault bars represent one standard divergence.
The infidelity of the generated state has iii main contributions: double \(|0\rangle \) state occupancy, double optical excitation and finite distinguishability of the photonsxviii,19. In the case of double \(|0\rangle \) land occupancy (which occurs with probability α), both communication qubits are in the \(|0\rangle \) land and have emitted a photon. Detection of one of these photons leads to false heralding of an entangled state. The second effect, double excitation, is due to the finite length of the optical pulse compared with the optical lifetime of the emitter. At that place is a finite chance that the communication qubit emits a photon during this pulse, is later re-excited and and so emits another photon, resulting in the qubit state being entangled with ii photons. Detection or loss of the first photon destroys the coherence of the qubit–photon entangled state and detection of the 2nd photon can then falsely herald the generation of an entangled state.
Crucially, false heralding events acquired by double \(|0\rangle \) country occupancy and double excitation are both accompanied past an extra emitted photon. Therefore, detection of this extra photon allows for unambiguous identification of such events and thus for existent-time rejection of faux heralding signals. We implement this rejection scheme by monitoring the off-resonant phonon-side band (PSB) detection path on both setups during and later the optical excitation (see Fig. 2a).
To investigate the upshot of this scheme, we generate entanglement on the individual links and extract the entanglement heralding events for which the PSB monitoring flagged the presence of an actress photon. For these events, we analyse the corresponding qubit measurements in the computational basis (Fig. 2c).
Nosotros identify two dissever regimes: one during the optical pulse (imperial) and one after the optical pulse (yellow). When a photon is detected on Alice's (Bob'due south) PSB detector during the optical pulse, we see that the outcome 01 (ten) is nigh probable (majestic information in Fig. 2c), showing that only one setup was in the \(|0\rangle \) state and thus that both detected photons originated from Alice (Bob). The detection of PSB photons during the optical pulse thus primarily flags double excitation errors. By dissimilarity, when a photon is detected later the optical pulse in either Alice's or Bob's PSB detector, the outcome 00 is nigh likely (yellowish data in Fig. 2c), indicating that both setups were in the \(|0\rangle \) country and emitted a photon. PSB photon detection later the optical pulse thus flags the double \(|0\rangle \) state occupancy error. We observe similar results to Fig. 2c for the entangled states generated on the Bob–Charlie link; see Extended Information Fig. 2. The comeback in fidelity from rejecting these faux heralding events in our experiment is set past the combined probability of occurrence (≈9%; meet Supplementary Information) multiplied by the probability to flag them (given here by the total PSB photon detection efficiency of ≈10%).
The third main source of adultery, the finite distinguishability, can ascend from frequency detunings between the emitted photonsxx. Whereas most of these detunings are eliminated upwards front end by the charge-resonance (CR) bank check before the outset of the protocol (see Supplementary Information), the communication qubits may yet be subject to a pocket-size amount of spectral diffusion. In our single-photon protocol, this leads to dephasing that is stronger for photons that are detected subsequently relative to the optical pulse. Past shortening our detection window, we tin can increment the fidelity of the entangled state at the expense of a lower entangling rate. For the experiments below (unless mentioned otherwise), nosotros use a detection window length of 15 ns. Effigy 2d summarizes the measured improvements on the individual links and the estimated effect on the Alice–Charlie entangled land fidelity. The increase of ≈3% is instrumental in pushing the teleportation fidelity above the classical bound.
Memory qubit coherence
In the preparation of the teleporter, we reliably preserve the Alice–Bob entangled link on the memory qubit, by aborting the sequence and starting over when the Bob–Charlie entangled state is not heralded within a fixed number of attempts, the timeout.
The 13C retentiveness qubits can exist controlled with loftier fidelity by means of the communication qubit, although they tin can be efficiently decoupled when no interaction is desired. Recent work showed that, in a magnetic field of 189 mT, entanglement generation attempts with the advice qubit practise not limit the retention dephasing fourth dimension \({T}_{2}^{\ast }\) (ref.18), opening the door to substantially extending the retentiveness preservation time with active coherence protection from the spin bathroom21. We realize this protection by integrating a decoupling π-pulse on the memory qubit into the experimental sequence that follows a heralding issue, while ensuring that all phases that are picked up owing to the probabilistic nature of the remote entangling process are compensated in real time (Fig. 3a).
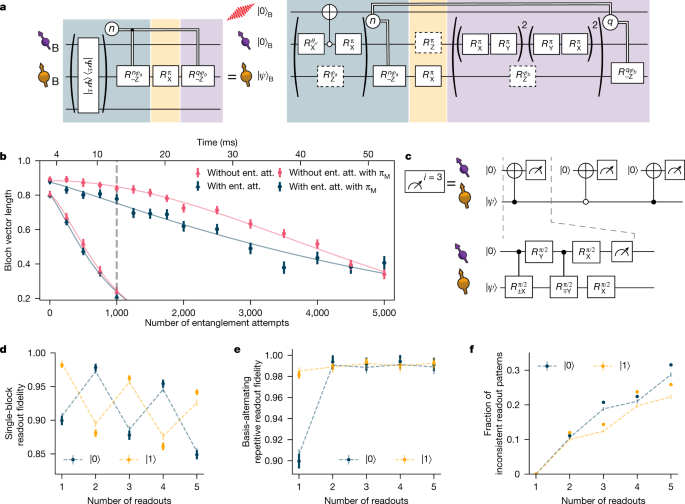
a, Gate sequence on Bob for entanglement generation with the communication qubit while preserving states stored on the memory qubit. Entanglement generation attempts are repeated until success or a predetermined timeout. On success in the northwardthursday attempt, a stage feed-forward is applied to maintain the correct reference frame of the memory qubitxviii, followed by a decoupling pulse on the memory qubit. The decoupling πM pulse causes a Z rotation on the advice qubit. Subsequently, we rephase the memory qubit for the same corporeality of time as information technology took to herald entanglement (by applying q blocks of XY8 decoupling sequences on the communication qubit, in which q depends on the number of entanglement attempts needed northward) and nosotros cease with another phase feed-forwards on the retentiveness qubit, to compensate for any stage picked upward during this decoupling. b, Bloch vector length of a superposition state stored on the memory qubit for different number of entanglement attempts or a time-equivalent look element. In the case of no decoupling (no πM) on the retention qubit, the gates in the xanthous shaded box in a are left out. The greyness dashed line indicates the chosen timeout of 1,000 entanglement attempts. c, Gate sequence for the basis-alternating repetitive readout of the memory qubit. d, Readout fidelity for each readout repetition, for states \(|0\rangle \) and \(|1\rangle \) eastward, Readout fidelity of the basis-alternate repetitive readout scheme for unlike number of readout repetitions. f, Fraction of inconsistent readout patterns for different number of readout repetitions. In d–f, the dashed lines testify a numerical model using measured parameters. All mistake confined correspond one standard deviation.
In Fig. 3b, we check the performance of this sequence by storing a superposition state on the memory qubit and measuring the Bloch vector length. We observe that, without the decoupling pulse, the decay of the Bloch vector length is not altered by the entanglement attempts, in line with previous findings18. Past contrast, when nosotros utilise the decoupling pulse, the decay is slowed downward by more than a factor of 6, yielding a N 1/e decay abiding of ≈five,300 entanglement attempts, the highest number reported so far for diamond devices. The difference in the shape of the decay indicates that intrinsic decoherence is no longer the simply limiting factor. The improved retentiveness coherence enables the states to utilize a timeout of i,000 entangling attempts, more than than double that of ref.xviii, which doubles the entanglement swapping rate.
Retention qubit readout
High-fidelity memory qubit readout is required both in the preparation of the teleporter (at Bob) and during the teleportation protocol itself (at Charlie). The retentiveness qubit is read out by mapping its state onto the communication qubit using quantum logic followed by single-shot readout of the communication qubit using state-dependent optical excitation and detection22. Owing to limited photon collection efficiency (≈10%) and finite cyclicity of the optical transition (≈99%), the advice qubit readout allegiance is different for \(|0\rangle \) and \(|i\rangle \) and the probability that the correct country was assigned is much larger if one or more photons were detected (assigned consequence 0) than if no photons were detected (assigned issue i)23. In previous work, nosotros circumvented this issue by workout on obtaining the upshot 0 (ref.xviii). Still, this approach scales unfavourably, as it forces the protocol to prematurely abort with probability >50% at each memory qubit readout.
We resolve this challenge by introducing a basis-alternating repetitive readout for the retentivity qubit (see Fig. 3c). The central signal of this readout strategy is, in contrast to before piece of work24, to alternatingly map the computational footing states of the memory qubit to the communication qubit state \(|0\rangle \) Effigy 3d shows the readout fidelities of the due northth readout repetition for the 2 initial states for the retention qubit on Bob (for Charlie, meet Extended Data Fig. iii). We clearly observe the expected alternating blueprint owing to the disproportion of the communication qubit readout fidelities. Notably, the readout allegiance decays but past ≈1% per readout, showing that the readout is more often than not not-demolition and several readouts are possible without losing the state.
Next, we assign the land using the first readout and continue the sequence merely when the consecutive readouts are consistent with the first readout. The subsequent readouts therefore add conviction to the assignment in the example of consistent outcomes, whereas cases of inconsistent outcomes (which take a college chance of indicating an incorrect assignment) are filtered out. In Fig. 3e, we plot the readout fidelity resulting from this strategy for up to five readouts, with the corresponding rejected fraction due to inconsistent outcomes plotted in Fig. 3f. Nosotros observe that using two readouts already eliminates most of the asymmetry, reducing the average adultery from ≈6% to below 1%. At this bespeak, the remaining observed infidelity mainly results from cases in which the retentiveness qubit was flipped during the outset readout block considering of imperfect retentivity qubit gates. For the experiments reported below (unless mentioned otherwise), we utilise two readout repetitions to benefit from a high average readout fidelity (Bob: 99.2(4)%, Charlie: 98.1(four)%) and a high probability to continue the sequence (Bob and Charlie: ≈88%).
Teleporting qubit states from Charlie to Alice
With all innovations described above implemented, we perform the protocol equally shown in Fig. 4a. Starting time, we generate entanglement between Alice and Bob and shop Bob's part of the entangled state on the memory qubit using a compiled Swap operation. 2nd, we generate entanglement between Bob and Charlie, while preserving the first entangled state on the memory qubit with the pulse sequence as described in Fig. 3a. Next, we perform a BSM on Bob followed past a CR check. We continue the sequence if the communication qubit readout yields consequence 0, the memory qubit readout gives a consequent outcome blueprint and the CR check is passed. At Charlie, we perform a quantum gate that depends on the effect of the BSM and on which detectors clicked during the two-node entanglement generation. Next, we swap the entangled land to the retention qubit. At this indicate, the teleporter is ready and Alice and Charlie share an entangled land with an estimated fidelity of 0.61.
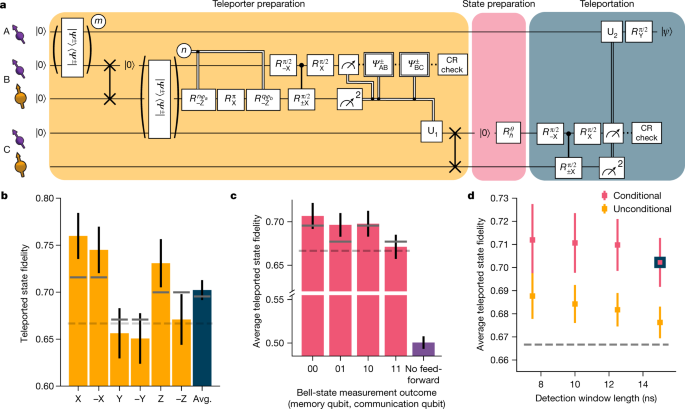
a, Circuit diagram of the teleportation protocol using notation defined in Fig. 3. m (n) is the number of attempts needed to herald entanglement for the AB (BC) entangled link. See the Supplementary Information for the full circuit diagram. b, Teleported state fidelities for the six central states and their average (Avg.). The gray lines show the expected fidelities from simulations. The dashed lines in b–d represent the classical bound of 2/three. c, Average teleported state fidelity for the different outcomes of the BSM on Charlie. The right-most bar shows the resulting fidelity when no feed-frontward operation on Alice would exist applied. The numerical values of the bar plots shown in b and c tin be found in Extended Data Tables 1 and ii. d, Average state fidelity for a conditional and an unconditional teleportation, for different detection window lengths of the ii-node entanglement generation processes. The blue-bordered data indicate is the same betoken equally shown in b. All error confined represent 1 standard divergence.
Afterward, we generate the qubit land to exist teleported, \(|\psi \rangle ,\) on Charlie's communication qubit and run the teleportation protocol. Outset, a BSM is performed on the advice and memory qubits at Charlie. With the exception of unconditional teleportation (discussed below), we only go along the sequence when we obtain a 0 outcome on the communication qubit, when nosotros take a consistent readout pattern on the memory qubit and when Charlie passes the CR check. The outcomes of the BSM are sent to Alice and, past applying the corresponding gate performance, we obtain \(|\psi \rangle \) on Alice'southward side.
We teleport the six fundamental states \((\pm {\rm{X}},\pm {\rm{Y}},\pm {\rm{Z}}),\) which form an unbiased set25, and measure the allegiance of the teleported states to the ideally prepared land (Fig. 4b). Nosotros find an boilerplate teleported land fidelity of F = 0.702(xi) at an experimental rate of 1/(117 southward). This value exceeds the classical bound of 2/iii by more than than three standard deviations, thereby proving the breakthrough nature of the protocol. We annotation that this value provides a lower spring to the true teleportation fidelity, equally the measured allegiance is decreased past errors in the grooming of the qubit states at Charlie (estimated to be 0.5%; see Supplementary Information).
The differences in allegiance between the teleported states arise from an interplay of errors in different parts of the protocol that either bear on all three axes (depolarizing errors) or affect only 2 axes (dephasing errors). These differences are qualitatively reproduced past our model (grey bars in Fig. 4b). In Fig. 4c, we plot the teleportation fidelity for each possible effect of the BSM. Attributable to the basis-alternating repetitive readout, the dependence on the 2nd bit (from the memory qubit readout) is small, whereas for the first bit (advice qubit readout), the best teleported state fidelity is achieved for upshot 0, due to the asymmetric readout fidelities. We as well analyse the case in which no feed-forrad is applied at Alice (meet Methods); equally expected, the average state fidelity reduces to a value consistent with a fully mixed land (fidelity F = 0.501(vii)), emphasizing the critical office of the feed-frontwards in the teleportation protocol.
Finally, we demonstrate that the network tin can achieve unconditional teleportation betwixt Alice and Charlie by using the BSM in a deterministic fashion. To this end, we revise the protocol at Charlie to accept both advice qubit outcomes, employ all retentiveness qubit readout patterns, including the inconsistent ones, and disregard the upshot of the CR check subsequently the BSM. Using this fully deterministic BSM lowers the average teleportation fidelity past a few pct (Fig. 4d). At the same time, shortening the detection windows of the 2-node entanglement generation is expected to yield an improvement in the fidelity, as discussed to a higher place. Nosotros find that, indeed, the average unconditional teleportation fidelity increases with shorter window lengths, reaching F = 0.688(x) for a length of 7.5 ns and a rate of 1/(100 s); run into Extended Information Fig. 4. The current breakthrough network is thus able to perform teleportation beyond the classical bound, even under the strict status that every land inserted into the teleporter exist transferred.
Outlook
In this work, we have realized unconditional qubit teleportation betwixt not-neighbouring nodes in a quantum network. The innovations introduced hither on retentivity qubit readout and protection during entanglement generation, as well as the real-fourth dimension rejection of simulated heralding signals, will exist instrumental in exploring more than complex protocols2,11,12,13,26. As well, these methods tin exist readily transferred to other platforms, such as the group IV color centres in diamond, the vacancy-related qubits in SiC and single rare-earth ions in solids27,28,29,30,31,32,33.
The development of an improved optical interface for the communication qubit34 will increment both the teleportation protocol rate and fidelity. Because of the improved retention qubit operation reported hither, the network already operates close to the threshold at which nodes can reliably deliver a remote entangled state while preserving previously stored quantum states in their retentivity qubits. With farther improvements, for instance, by integrating multi-pulse memory decoupling sequences21 into the entanglement generation, demonstration of deterministic qubit teleportation (with no pre-shared entangled state) may come within reach, which opens the door to exploring applications that call the teleportation routine several times. In addition, future piece of work will focus on further improving the stage stabilization and extending the current schemes for use in deployed fibre35.
Finally, by implementing a recently proposed link layer protocol36, qubit teleportation and applications making utilise of the teleportation primitive may be executed and tested on the network through platform-independent control software, an of import prerequisite for a large-scale future network.
Methods
Experimental setup
The basics of the experimental setup are described in ref.xviii. In the electric current experiment, Charlie has access to a carbon-13 nuclear spin that acts as a retentivity qubit. The parameters used for the memory qubits of Bob and Charlie can be found in Extended Data Tabular array iii. Furthermore, we have set a classical communication channel betwixt Charlie and Alice, such that Charlie tin directly send the results of the BSM to Alice.
Temporal selection of heralding photons
To eliminate any reflected excitation light in the heralding detectors, nosotros make use of a cross-polarization scheme and perform temporal selection of the detected photons as described in ref.37. We start the detection windows 4 ns (5 ns) after the highest intensity point of the excitation pulse, for the AB (BC) entangled link, to ensure sufficient suppression of excitation laser lite in the detection window.
Retention qubit coherence Bob
We use the sequence described in Fig. 3a to preserve the state of the memory qubit during entanglement attempts. To characterize the decoupling sequence, we compare information technology to the sequence in which nosotros practice non apply the decoupling pulse on the memory qubit and/or the sequence in which we idle instead of performing entanglement attempts. We narrate the coherence of the memory qubit by storing the six cardinal states. Nosotros average the results for the eigenstates \((|0\rangle ,|1\rangle )\) and superposition states \((|\pm {\rm{X}}\rangle {\rm{and}}|\pm {\rm{Y}}\rangle ).\) In Extended Data Fig. 5a, we plot the Bloch vector length \(b=\sqrt{{b}_{x}^{ii}+{b}_{y}^{2}+{b}_{z}^{ii}},\) with b i the Bloch vector component in direction i.
Over the measured range, the eigenstates show niggling decay. The disuse of the superposition states is fitted with the function \(f(10)=A{{\rm{e}}}^{-{(10/{North}_{1/{\rm{e}}})}^{northward}}.\) The fitted parameters tin be institute in Extended Data Fig. 5b.
The use of the decoupling pulse πM on the memory qubit increases the North one/e by more than a factor of vi. Moreover, the initial Bloch vector length A is higher with the πThou pulse. This is mainly explained by the second circular of phase stabilizationxviii in between swapping the state onto the retentivity qubit and starting the entanglement generation procedure. The phase stabilization takes ≈350 μs and, during this time, the memory qubit is bailiwick to intrinsic \({T}_{ii}^{\ast }\) dephasing, which can be efficiently decoupled using the πG pulse.
Communication qubit coherence
In various parts of the protocol, we decouple the advice qubits from the spin bath environment to extend their coherence time. On Alice, we get-go the decoupling when the start entangled link is established and end when the results of the BSM to teleport the state are sent by Charlie. On Bob, nosotros decouple the communication qubit when the retentiveness qubit is being rephased. On Charlie, the communication qubit is decoupled from the point that entanglement with Bob is heralded up to the point at which Bob has finished the BSM, performed the CR check and has communicated the results. All these decoupling times are dependent on how many entanglement attempts are needed to generate the entangled link between Bob and Charlie.
Nosotros characterize the average state fidelities for different decoupling times; see Extended Data Fig. 6a. Nosotros investigate eigenstates and superposition states separately. Nosotros fit the fidelity with the function \(f(t)=A{{\rm{e}}}^{-{(t/{\tau }_{{\rm{coh}}})}^{north}}+0.5.\) The fitted parameters are summarized in Extended Data Fig. 6b. For each setup, the minimum and maximum decoupling times used are indicated by the shaded regions in Extended Data Fig. 6a. The left-most border is the decoupling time when the first entanglement attempt on Bob and Charlie would be successful and the right-almost border is when the concluding try before the timeout of 1,000 attempts would herald the entangled state.
Model of the teleported country
A detailed model of the teleported state tin can be plant at https://doi.org/ten.4121/16645969. The model comprises elements from ref.eighteen and is further extended for the teleportation protocol. Nosotros have the following noise sources into account:
-
Imperfect Bell states between Alice and Bob, and betwixt Bob and Charlie.
-
Dephasing of the memory qubit of Bob during entanglement generation between Bob and Charlie.
-
Depolarizing racket on the retention qubits of Bob and Charlie, owing to imperfect initialization and bandy gates.
-
Readout errors on the communication qubits of Bob and Charlie and readout errors on the retention qubits of Bob and Charlie when using the footing-alternating readout scheme, which result in incorrect feed-frontward gate operations after the BSMs.
-
Depolarizing dissonance on Alice during the decoupling sequence.
-
Ionization probability on Alice.
An overview of the input parameters and the effect of the different error sources are given in Extended Data Table iv.
Calculation of teleported state fidelity without feed-forrard functioning
In Fig. 4c, nosotros testify the fidelity of the teleported state in case no feed-forwards operations would have been practical on Alice. To excerpt this data, nosotros follow the same method every bit in ref.9. We perform classical bit flips on the measurement outcomes to counteract the issue of the feed-forward gate operations (every bit if the gate was non applied) for each BSM consequence. Nosotros practice this for all half dozen primal states and compute the average allegiance. Nosotros presume the errors of the gate in the feed-forward operations to be small.
Data availability
The datasets that back up this manuscript and the software to analyse them are available at https://doi.org/10.4121/16645969.
References
-
Kimble, H. J. The quantum internet. Nature 453, 1023–1030 (2008).
-
Wehner, S., Elkouss, D. & Hanson, R. Quantum internet: a vision for the road alee. Science 362, eaam9288 (2018).
-
Bennett, C. H. et al. Teleporting an unknown quantum country via dual classical and Einstein-Podolsky-Rosen channels. Phys. Rev. Lett. 70, 1895–1899 (1993).
-
Bouwmeester, D. et al. Experimental quantum teleportation. Nature 390, 575–579 (1997).
-
Boschi, D., Branca, Southward., De Martini, F., Hardy, L. & Popescu, Due south. Experimental realization of teleporting an unknown pure quantum country via dual classical and Einstein-Podolsky-Rosen channels. Phys. Rev. Lett. 80, 1121–1125 (1998).
-
Furusawa, A. et al. Unconditional quantum teleportation. Science 282, 706–709 (1998).
-
Olmschenk, S. et al. Quantum teleportation between distant matter qubits. Science 323, 486–489 (2009).
-
Nölleke, C. et al. Efficient teleportation between remote unmarried-atom quantum memories. Phys. Rev. Lett. 110, 140403 (2013).
-
Pfaff, W. et al. Unconditional quantum teleportation between afar solid-land quantum bits. Science 345, 532–535 (2014).
-
Langenfeld, S. et al. Quantum teleportation between remote qubit memories with only a single photon as a resource. Phys. Rev. Lett. 126, 130502 (2021).
-
Ben-Or, M., Crépeau, C., Gottesman, D., Hassidim, A. & Smith, A. Secure multiparty quantum ciphering with (but) a strict honest bulk. In Proc. 2006 47th Almanac IEEE Symposium on Foundations of Computer Science (FOCS'06) 249–258 (IEEE, 2006).
-
Arora, A. S., Roland, J. & Weis, S. Quantum weak coin flipping. In Proc. 51st Annual ACM Symposium on Theory of Computing (STOC 2019) 205–216 (ACM, 2019).
-
Van Meter, R. Breakthrough Networking (Wiley, 2014).
-
Bao, 10.-H. et al. Quantum teleportation between remote diminutive-ensemble quantum memories. Proc. Natl Acad. Sci. 109, 20347–20351 (2012).
-
Briegel, H.-J., Dür, W., Cirac, J. I. & Zoller, P. Breakthrough repeaters: the office of imperfect local operations in breakthrough communication. Phys. Rev. Lett. 81, 5932–5935 (1998).
-
Cabrillo, C., Cirac, J. I., García-Fernández, P. & Zoller, P. Cosmos of entangled states of distant atoms by interference. Phys. Rev. A 59, 1025–1033 (1999).
-
Bose, S., Knight, P. L., Plenio, M. B. & Vedral, V. Proposal for teleportation of an atomic state via cavity disuse. Phys. Rev. Lett. 83, 5158–5161 (1999).
-
Pompili, M. et al. Realization of a multinode breakthrough network of remote solid-land qubits. Science 372, 259–264 (2021).
-
Humphreys, P. C. et al. Deterministic delivery of remote entanglement on a quantum network. Nature 558, 268–273 (2018).
-
Legero, T., Wilk, T., Kuhn, A. & Rempe, Thou. Time-resolved two-photon quantum interference. Appl. Phys. B 77, 797–802 (2003).
-
Bradley, C. et al. A ten-qubit solid-state spin register with breakthrough memory up to one minute. Phys. Rev. X nine, 031045 (2019).
-
Cramer, J. et al. Repeated quantum error correction on a continuously encoded qubit past real-time feedback. Nat. Commun. 7, 11526 (2016).
-
Robledo, L. et al. High-fidelity projective read-out of a solid-land spin quantum register. Nature 477, 574–578 (2011).
-
Jiang, L. et al. Repetitive readout of a single electronic spin via quantum logic with nuclear spin ancillae. Science 326, 267–272 (2009).
-
van Enk, Southward. J., Lütkenhaus, Due north. & Kimble, H. J. Experimental procedures for entanglement verification. Phys. Rev. A 75, 052318 (2007).
-
Broadbent, A., Fitzsimons, J. & Kashefi, E. Universal bullheaded breakthrough ciphering. In Proc. 2009 50th Annual IEEE Symposium on Foundations of Computer Science 517–526 (IEEE, 2009).
-
Rose, B. C. et al. Observation of an environmentally insensitive solid-state spin defect in diamond. Science 361, 60–63 (2018).
-
Nguyen, C. et al. Quantum network nodes based on diamond qubits with an efficient nanophotonic interface. Phys. Rev. Lett. 123, 183602 (2019).
-
Trusheim, G. Eastward. et al. Transform-limited photons from a coherent tin-vacancy spin in diamond. Phys. Rev. Lett. 124, 023602 (2020).
-
Son, N. T. et al. Developing silicon carbide for breakthrough spintronics. Appl. Phys. Lett. 116, 190501 (2020).
-
Lukin, D. M., Guidry, 1000. A. & Vučković, J. Integrated quantum photonics with silicon carbide: challenges and prospects. PRX Quantum i, 020102 (2020).
-
Kindem, J. M. et al. Control and single-shot readout of an ion embedded in a nanophotonic cavity. Nature 580, 201–204 (2020).
-
Chen, Southward., Raha, M., Phenicie, C. M., Ourari, South. & Thompson, J. D. Parallel single-shot measurement and coherent command of solid-state spins beneath the diffraction limit. Scientific discipline 370, 592–595 (2020).
-
Ruf, G., Wan, North. H., Choi, H., Englund, D. & Hanson, R. Quantum networks based on colour centers in diamond. J. Appl. Phys. 130, 070901 (2021).
-
Grein, Thousand. East., Stevens, M. L., Hardy, N. D. & Benjamin Dixon, P. Stabilization of long, deployed optical cobweb links for quantum networks. In Proc. 2017 Conference on Lasers and Electro-Optics (CLEO 2017) 1–2 (IEEE, 2017).
-
Dahlberg, A. et al. A link layer protocol for quantum networks. In Proc. ACM Special Interest Group on Data Communication (SIGCOMM '19) 159–173, (ACM, 2019).
-
Hensen, B. et al. Loophole-free Bell inequality violation using electron spins separated by one.three kilometres. Nature 526, 682–686 (2015).
Acknowledgements
We thank S. Wehner, T. Taminiau, C. Bradley and H. de Riedmatten for discussions. We acknowledge fiscal back up from the Eu Flagship on Breakthrough Technologies through the project Breakthrough Internet Brotherhood (European union Horizon 2020, grant agreement no. 820445); from the European Research Council (ERC) through an ERC Consolidator Grant (grant agreement no. 772627 to R.H.); from the Netherlands Organisation for Scientific Research (NWO) through a VICI grant (project no. 680-47-624) and the Zwaartekracht plan Quantum Software Consortium (project no. 024.003.037/3368). S.B. acknowledges support from an Erwin-Schrödinger fellowship (QuantNet, no. J 4229-N27) of the Austrian National Science Foundation (FWF).
Writer information
Authors and Affiliations
Contributions
Due south.L.Due north.H., G.P. and R.H. devised the experiment. S.Fifty.N.H., Chiliad.P. and H.1000.C.B. carried out the experiments and nerveless the data. S.Fifty.N.H., M.P., H.K.C.B. and S.B. prepared the experimental appliance. J.B. developed the breakthrough-optical model. S.Fifty.N.H. and R.H. wrote the main manuscript, with input from all authors. S.50.N.H., 1000.P. and J.B. wrote the supplementary materials, with input from all authors. S.L.N.H. and M.P. analysed the data and discussed with all authors. R.H. supervised the research.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Peer review
Peer review data
Nature thanks Florian Kaiser and the other, bearding, reviewer(s) for their contribution to the peer review of this work. Peer reviewer reports are available.
Additional information
Publisher's note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Extended data figures and tables
Extended Data Fig. 1 PSB-flagged correlations Alice–Bob.
Meridian, histograms of the detected PSB photons conditioned on a simultaneous ZPL detection in the entanglement generation attempt, for Alice (left) and Bob (right). Lesser, respective measured correlations in all bases. The grey bars in the Z footing represent the simulated values. For the Ten and Y bases, one would wait a probability of 0.25 for all outcomes. All error bars represent one standard difference.
Extended Information Fig. 2 PSB-flagged correlations Bob–Charlie.
Top, histograms of the detected PSB photons conditioned on a simultaneous ZPL detection in the entanglement generation effort, for Bob (left) and Charlie (right). Bottom, corresponding measured correlations in all bases. The grey bars in the Z basis stand for the false values. For the X and Y bases, one would expect a probability of 0.25 for all outcomes. All error bars correspond one standard departure.
Extended Data Fig. 3 Ground-alternating repetitive readout.
Footing-alternating repetitive (BAR) readout results for Charlie's memory qubit. a, Readout fidelity for each readout repetition, for states \(|0\rangle \) and \(|1\rangle .\) b, Readout fidelity of the BAR readout scheme for dissimilar number of readout repetitions. c, Fraction of inconsistent readout patterns for unlike number of readout repetitions. The dashed lines represent a numerical model using measured parameters, which can exist institute at https://doi.org/10.4121/16645969. All error bars stand for one standard deviation.
Extended Data Fig. 4 Experimental rates.
Experimental rates of the conditional and unconditional teleportation protocol for different detection window lengths in the two-node entanglement generation.
Extended Information Fig. 5 Memory qubit coherence.
a, Coherence of Bob'south memory qubit for superposition states (triangles and circles) and eigenstates (squares and diamonds). We perform the sequence as described in the main text with and without the decoupling pulse πM on the memory qubit, the dark blue and purple points, respectively. Furthermore, we perform the sequence with a look time instead of entanglement attempts with (pinkish points) and without (yellowish points) the decoupling pulse. The gray dashed line indicates the timeout of the entanglement generation procedure used in the teleportation protocol. b, Fitted parameters for the memory coherence decay of the superposition states. All error bars stand for i standard deviation.
Extended Data Fig. 6 Communication qubit coherence.
a, Decoupling of the communication qubits. The boilerplate state fidelity is plotted for unlike decoupling times for each setup. The shaded area represents the decoupling times used in the teleportation protocol. b, Fitted parameters for average country fidelity during communication qubit decoupling. All error bars represent one standard deviation.
Supplementary data
Rights and permissions
Open Access This article is licensed under a Creative Eatables Attribution 4.0 International License, which permits use, sharing, accommodation, distribution and reproduction in any medium or format, as long every bit you give appropriate credit to the original writer(due south) and the source, provide a link to the Creative Eatables license, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons license, unless indicated otherwise in a credit line to the material. If textile is not included in the article'southward Creative Eatables license and your intended utilize is non permitted by statutory regulation or exceeds the permitted use, you volition need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/iv.0/.
Reprints and Permissions
About this article
Cite this article
Hermans, Due south.L.North., Pompili, M., Beukers, H.K.C. et al. Qubit teleportation betwixt non-neighbouring nodes in a quantum network. Nature 605, 663–668 (2022). https://doi.org/x.1038/s41586-022-04697-y
-
Received:
-
Accepted:
-
Published:
-
Issue Appointment:
-
DOI : https://doi.org/10.1038/s41586-022-04697-y
Farther reading
Comments
Past submitting a comment you lot concord to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag information technology every bit inappropriate.
State Of Nature Node Shape,
Source: https://www.nature.com/articles/s41586-022-04697-y
Posted by: harrisfroplithe.blogspot.com


0 Response to "State Of Nature Node Shape"
Post a Comment